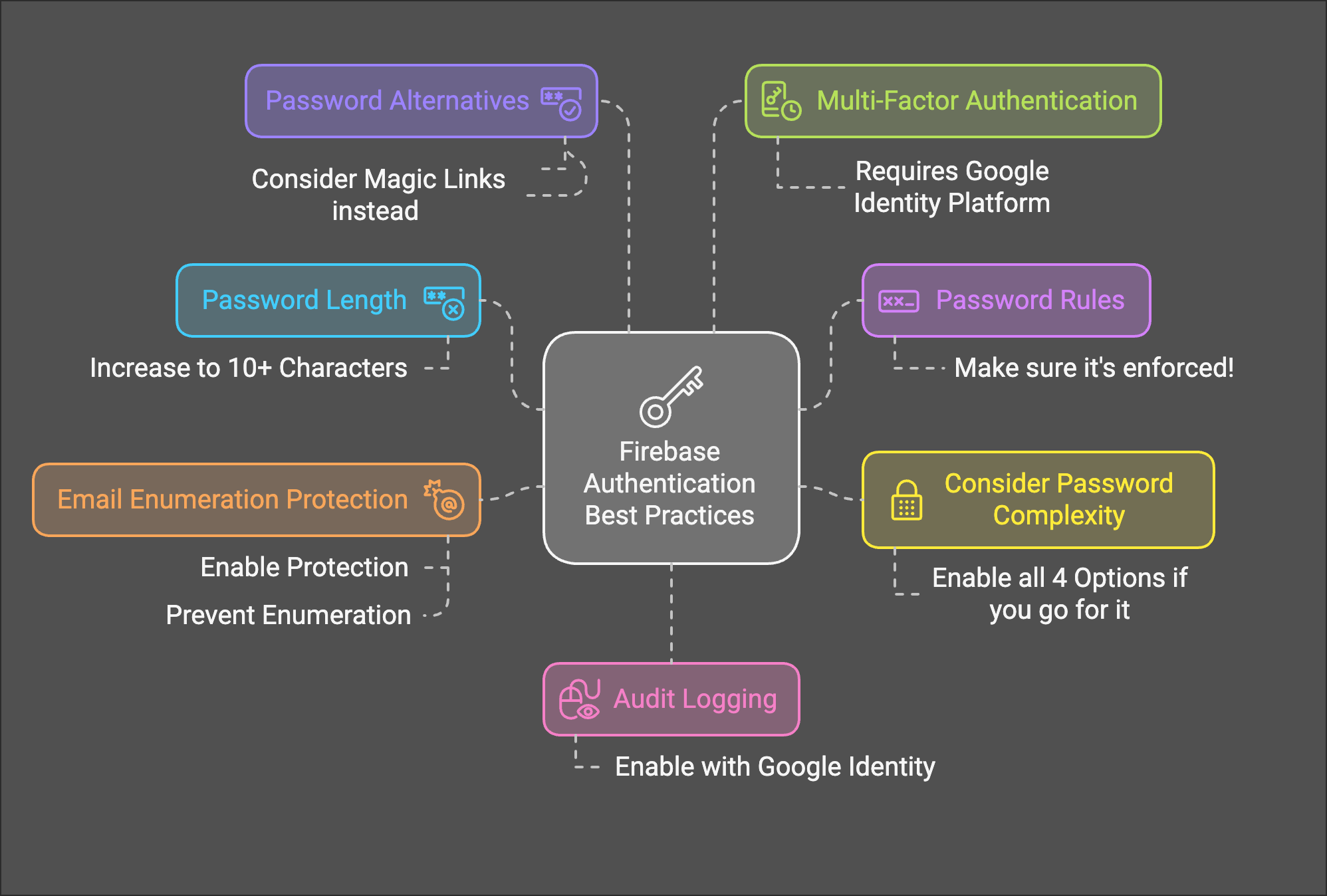
Firebase authentication - Best practices for password requirements
Introduction
Firebase Authentication is a fantastic tool for managing user sign-ups and logins in your app. It’s easy to set up, handles a lot of the heavy lifting for you, and provides a seamless user experience. But, despite its ease of use - it comes with bizarrely insecure default options. This blog post will dive into some essential best practices for locking down your Firebase Authentication, particularly when using the email/password provider.
In building out Flames Shield - a Firebase security and compliance dashboard - we’ve implemented a dashboard to monitor best practices in Firebase authentication, and as part of that we want to share those practices and how to implement
Before we start
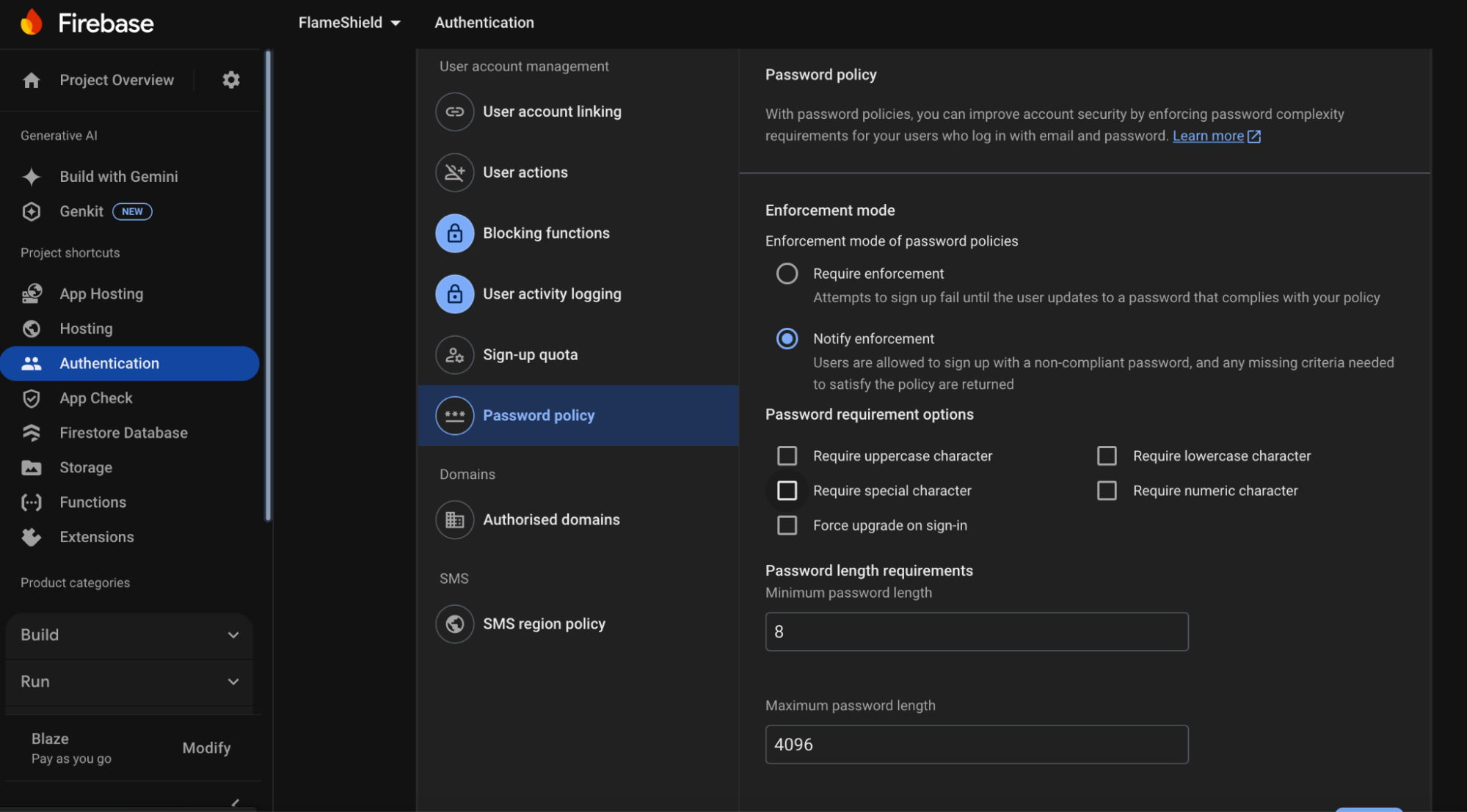
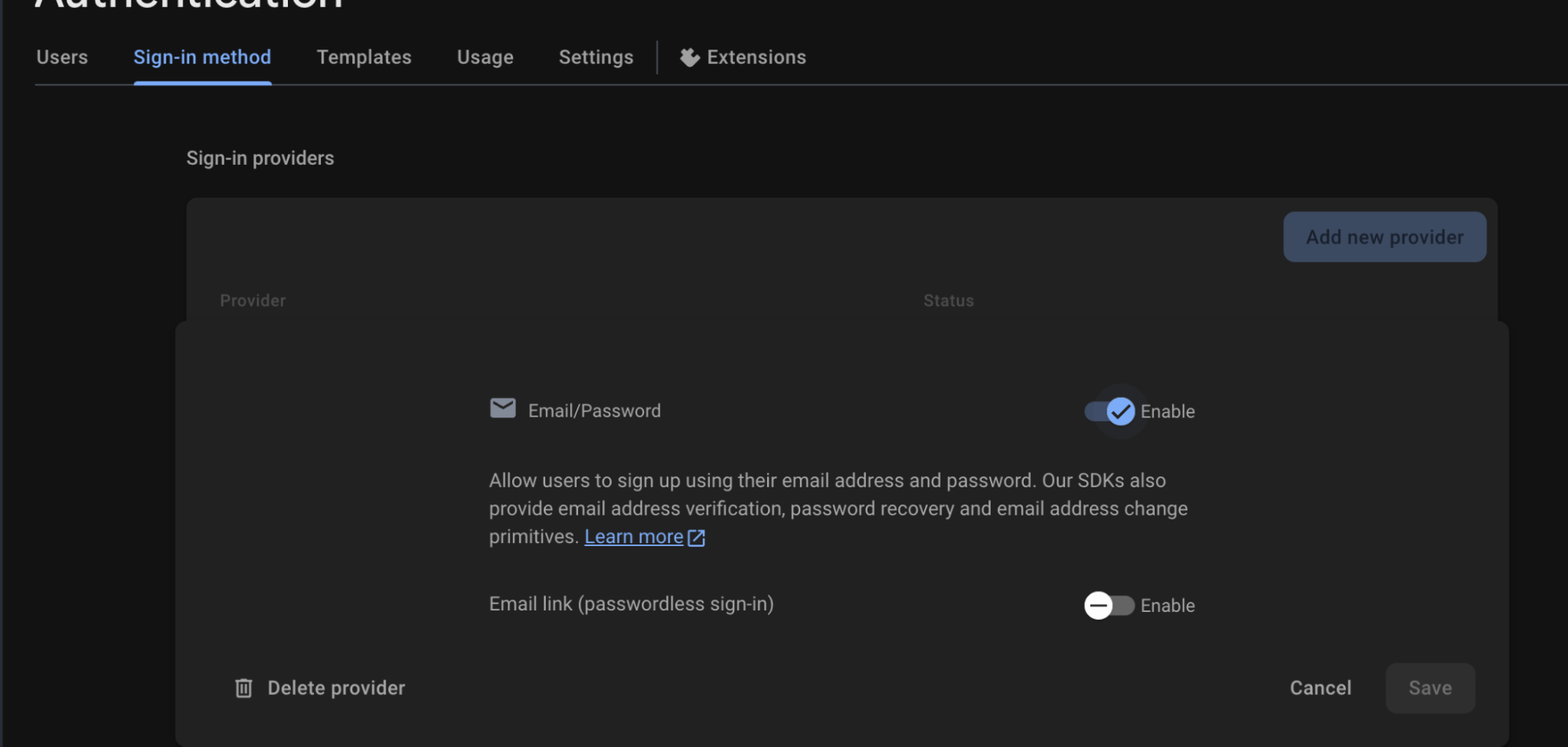
To make these changes, you’ll want to do them in the firebase console. Go to your project’s authentication settings and you should see a page like this:
Best Practices for Email/Password Authentication
Here are some key best practices to keep your Firebase Authentication secure when using email and password sign-in:
1. Ditch the Default Password Length
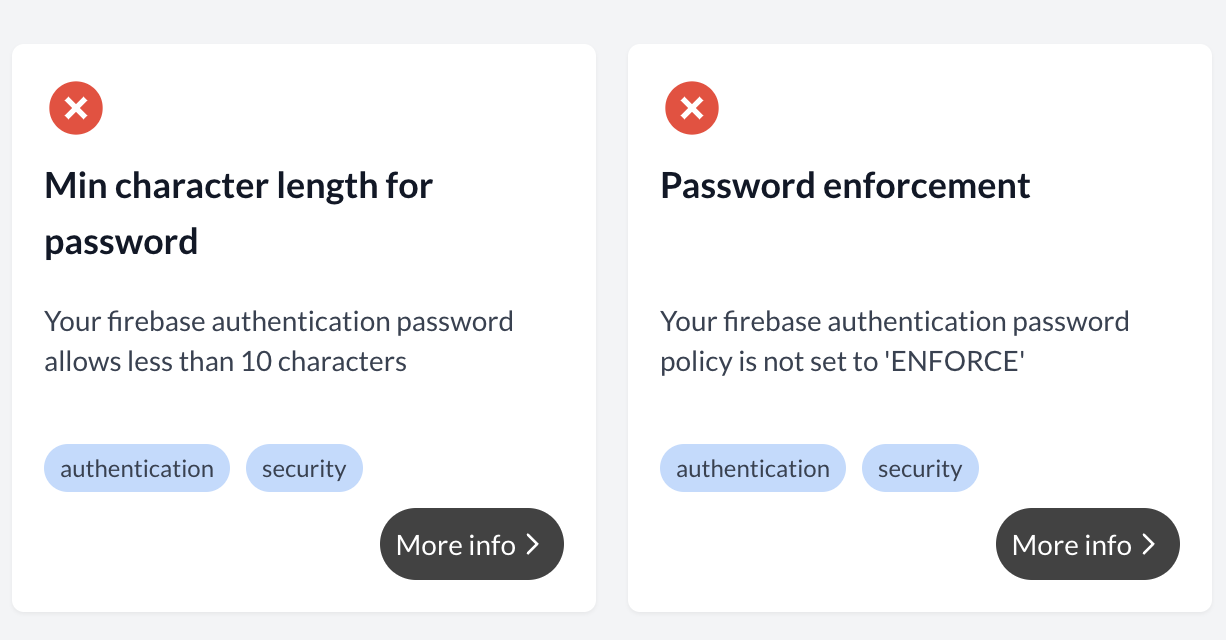
Firebase Authentication, by default, sets the minimum password length to a measly 6 characters - same as my phone pin. That’s simply not enough in today’s world of sophisticated hacking tools. We need to beef that up!
Recommendation: Increase the minimum password length to at least 10 characters, preferably 12 or more. This significantly increases the time and resources needed for brute-force attacks to succeed. You can easily adjust this in your Firebase project settings - (hint, it’s the “password length requirements” field).
Note: The default minimum password length is 6 characters, and password policy enforcement must be explicitly enabled in your Firebase project settings. For more details, see Firebase password policy documentation.
2. Enforce Password Rules!
Given that you’re going to the trouble of updating your password policy, it seems silly to not enforce it. For reasons unknown, Firebase by default has ‘password enforcement mode’ set to false (in the image it’s set to “notify enforcement” rather than “require enforcement”. This is a bit strange, and
Recommendation: Turn enforcement Mode ON: To enable enforcement mode in your Firebase project settings to ensure that all new passwords (and password changes) adhere to your defined rules.
3. Password complexity - maybe?
Best practices around password complexity have moved on a bit - famously, the UK’s NCSC - suggest using three random words, rather than complexity (read more). On the other hand, they also advocate the use of password managers - a 50 character password with special characters, numbers upper and lowercase stored in a password manager is a fairly strong defence.
So, you’ll need to make a call - do you want to mandate password complexity rules; and if not do you want to bump the password complexity length?
Recommendation: Think about password complexity, and if you do choose to set it tick all 4 options above.
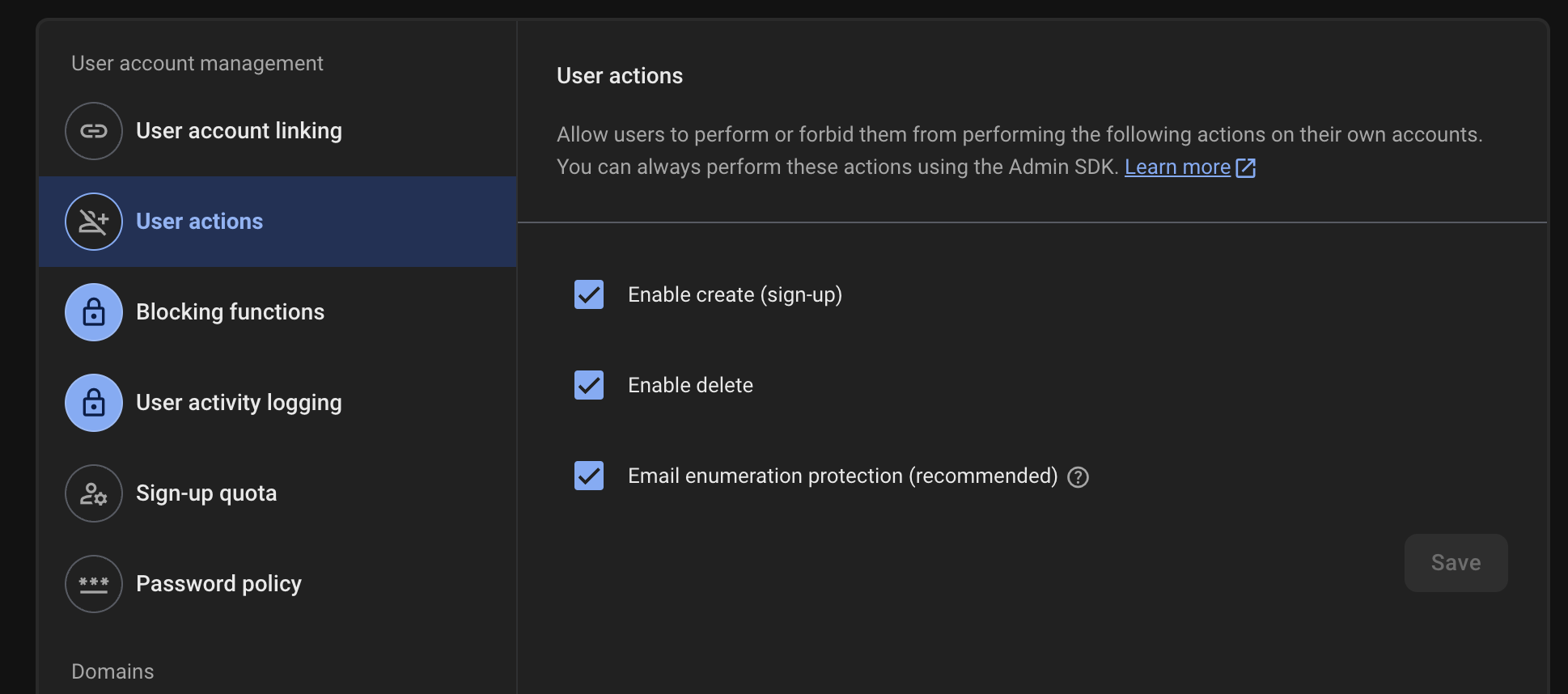
4. Enable Email Enumeration Protection
Email enumeration is a type of brute-force attack in which a malicious actor attempts to guess or confirm users in a system by passing an email address to the API and checking the response. Without email enumeration protection,Specifically, an attacker can try to ‘guess’ which emails are in the system by sending an email to your login, and can work out from the response if the email exists or not by the responding error code (e.g. it will return a EMAIL_NOT_FOUND if the email doesn’t exist, and EMAIL_EXISTS it it does).
With Identity protection enabled, the response from the API doesn’t give these clues away. There are some downsides, namely because you can’t use functions like fetchSignInMethodsForEmail which can be useful for UX - but the upside is that it makes it harder to perform email enumeration attacks.
You can read more here: Enable or disable email enumeration protection
Recommendation: Email enumeration protection. This one’s on a slightly different tab, but we suggest you enable email enumeration protection as in the screenshot below.
5. Consider disabling passwords altogether
Passwords have long been the bane of the security industry, and while stories about how they were never meant to be used for internet security are usually apocryphal, the industry has long been searching for alternatives.
Within Firebase, there are a few options - obviously, login with google and other social platforms is an option - but another one that become more widespread in recent user is ‘Magic links’ - where there aren’t any passwords at all, and instead users get a link emailed to them when they want to login.
A full discussion is beyond the scope of this post, but if you are interested in Passwords vs Magic-links i’d urge you read this: link
Recommendation: Consider removing passwords altogether. If you chose to do it, simply turn ‘off’ the email/password and toggle on the ‘password links’ - obviously, you’ll need to update your UI code to accommodate the new login flow!
Advanced Security
There are additional options available if you upgrade your account to Google Identity platform - there are a few extras that come with this, but there are two in particular if you’re considering the upgrade worth knowing about
Multi factor authentication
Multi-factor authentication is a type of auth whereby a user has to prove their identity using two different mechanisms. This type of authentication is thought to make an account 99% less likely to be attacked which is a compelling reason to consider it. That said, the additional cost, complexity and friction in login might be overkill for your application - it’s a call you have to make yourself!
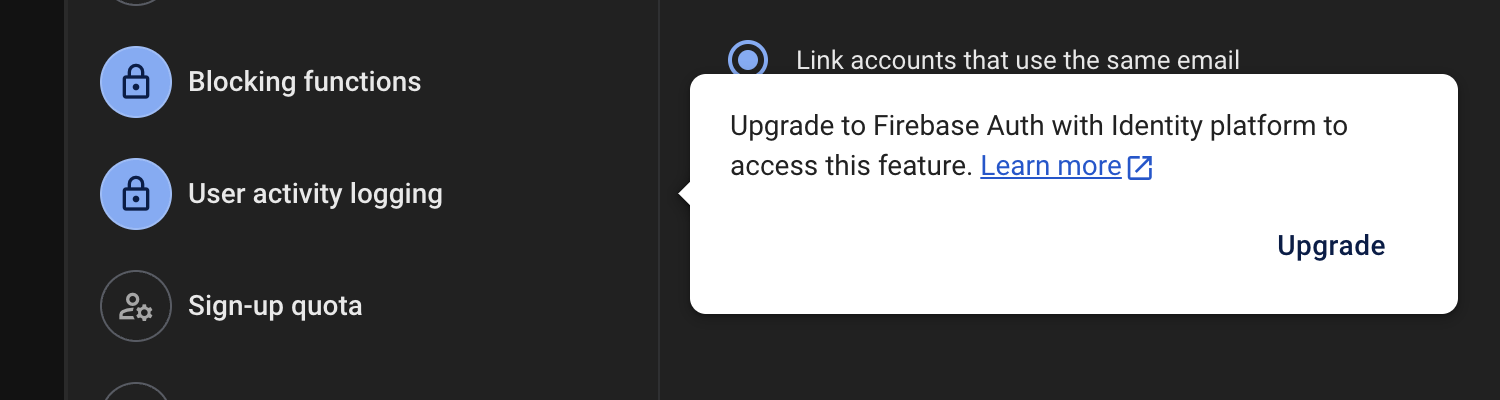
User activity and audit logging
A common setup in enterprise setups is to audit user logins and activity, again - this is part of the “Firebase with google identity platform” offering - but being able to track logins is often a key insight that’s important for sensitive applications where ’non-repudiation’ is key (particularly finance), but also useful post-incident when trying to piece together the anatomy of an attack on your system or application. To configure this one - check the screenshot below
Conclusion
Securing your Firebase Authentication is an ongoing process. By implementing these best practices, especially regarding password length, enforcement, and exploring passwordless options like email link authentication, you can significantly strengthen your app’s security and protect your users’ valuable data. Remember to strike a balance between robust security and a user-friendly experience. Happy coding, and stay secure!