From Vibe-Coded to Production-Ready: A Practical Guide for Firebase Studio Projects

You’ve built something in Firebase Studio. It works. People like it. But right now it’s more “prototype” than “production-ready app.”
Maybe you’re a product manager, designer, or entrepreneur who just wanted to prove an idea. Now it’s time to put it in front of real users — without it falling over, leaking data, or running up a big bill.
The good news: you don’t need to write code. You just need to know where to click in the Firebase Console and what to ask Firebase Studio’s prompter.
Lock Down Firestore Security Rules
Why: This is the biggest risk — leaving your database open to the world. Public access is the biggest risk, but you also want to check for other vulnerabilities that might leave you exposed. Check https://security.flamesshield.com/firestore/ for a more comprehensive list.
Check in the console:
- Go to Firestore Database → Rules.
- If you see:your database is public. Anyone can read/write everything.
1allow read, write: if true;
Fix in the console:
- Go to Firestore Database → Rules.
- Replace the public rules with user-specific access:
1 2 3 4 5 6 7 8rules_version = '2'; service cloud.firestore { match /databases/{database}/documents { match /users/{userId} { allow read, write: if request.auth != null && request.auth.uid == userId; } } }
Extra step: Use Rules Playground in the console (top right) to test:
- Try “Unauthenticated user” → should be denied.
- Try “Authenticated but different UID” → should be denied.
Fix Your Firestore Data Structure
Why: Bad structure = slow queries, high bills.
Check in the console:
Go to Firestore Database → Data.
Look at your top-level collections. Do you only have one big collection? That’s a red flag.
Open some documents. Are there giant arrays (like hundreds of items in one field)? Those should be moved into subcollections.
Prompt in Studio:
Restructure my Firestore so I have one collection for users, one for orders, and one for messages.
Any lists should be subcollections. Add pagination (limit 20) for large lists.
Optimise Reads & Writes (Save Money)
Why: Firestore charges per read/write. A few bad queries can explode costs.
Check in the console:
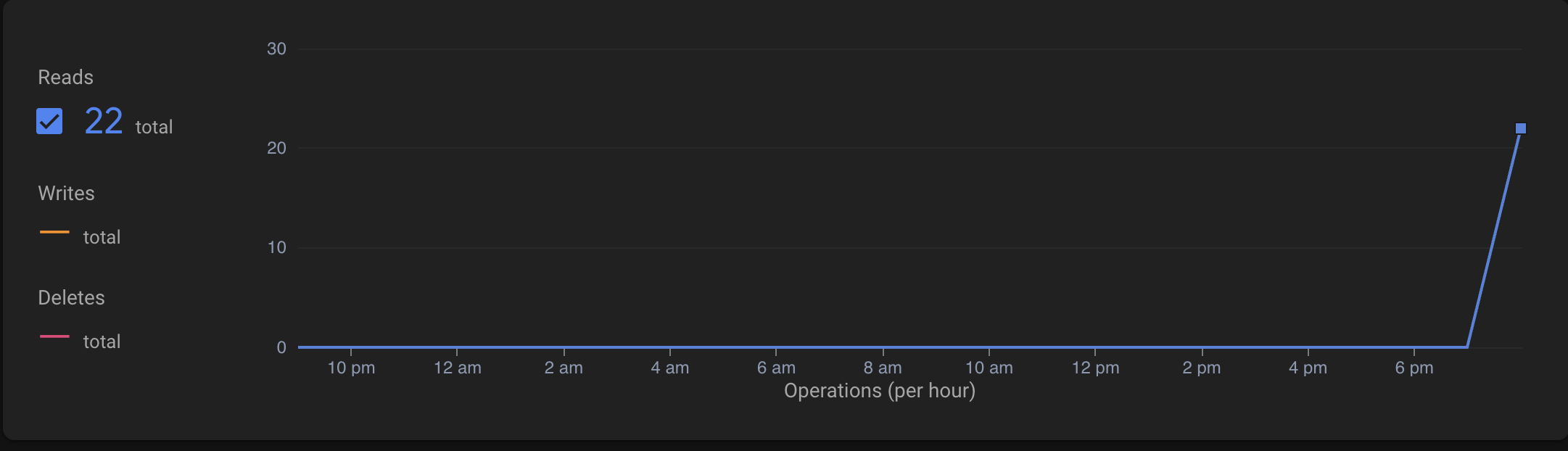
Go to Firestore Database → Usage.
Look at “Document reads per day.” Is it thousands even though you only have a few test users? That’s waste.
Prompt in Studio:
List all queries in this app that fetch entire collections. Change them so they only load documents for the current user, and add a limit of 20 with pagination.
Replace real-time listeners with one-time fetches everywhere except chat messages.
Make Authentication Production-Safe
Why: Prototypes often leave all providers open. That’s risky.
Check in the console:
- Go to Authentication → Sign-in method.
- Look at the list. Are Facebook, Twitter, GitHub all enabled even if you don’t use them? Disable them.
- Go to Authentication → Templates. Do password reset and email verification emails mention your app name?
Prompt in Studio:
Disable all sign-in methods except Google and Email/Password.
Require email verification before users can sign in.
Want to go deeper? For comprehensive authentication security including password policies, email enumeration protection, and advanced security options, check out our detailed guide: Firebase Authentication Best Practices.
Secure Cloud Storage
Why: Firebase Storage often gets overlooked, but it’s just as risky as Firestore if misconfigured.
Check in the console:
- Go to Storage → Rules.
- If you see:your storage is public. Anyone can upload/download files.
1allow read, write: if true;
Fix in the console:
Replace public rules with authenticated access:
| |
Extra considerations:
- File size limits: Set maximum upload sizes in your storage rules (e.g.,
request.resource.size < 5 * 1024 * 1024for 5MB). - File types: Restrict allowed file types if needed (e.g., only images).
- CORS: If users upload from your web app, ensure CORS is configured. For detailed CORS setup instructions, see our complete CORS guide. Quick setup: Go to Google Cloud Console → Storage → Browser → your bucket → Permissions → CORS.
Keep Secrets Out of the Frontend
Why: Firebase config keys are fine in the browser. Real secrets are not.
Check in the console:
Go to Project Settings → Service Accounts. If you see JSON keys, those must never be pasted into frontend code or Studio.
If you’re using third-party services (Stripe, Mailgun, etc.), check their docs: the keys labelled “Secret” or “Private” belong only on a server, not in your app.
Prompt in Studio (if you find a secret):
Move this third-party API call into a secure backend so the secret key is not exposed in the browser.
Protect Against Billing Spikes
Why: Firebase pricing is usage-based. If someone accidentally (or deliberately) floods your app with reads/writes, you could see a nasty surprise bill.
For extra safety, use a kill switch service (like FlameShield) that can automatically detach your billing account if spend goes over a set threshold.
This means:
- If usage suddenly explodes, your app stops instead of draining your bank account.
- You can always re-enable billing once you’ve investigated.
Avoid the Classic Vibe-Coded Pitfalls
Quick checks to run before launch:
- Open database? → Check Firestore rules for
if true. - Loading entire collections? → Check Usage graph; ask Studio to add limits.
- Dev and prod mixed? → Check Project ID in console; create a new project for prod if needed.
- No monitoring? → In Performance Monitoring, click Enable. In Billing → Budgets, set alerts.
Prompt in Studio:
Enable performance monitoring for my app and set a budget alert for when spend exceeds $20.
Pre-Launch Checklist (Console + Studio) ✅
- Firestore collections structured (Console → Firestore → Data)
- Queries limited & filtered (Prompt: “List all queries fetching entire collections…”)
- Auth providers trimmed (Console → Authentication → Sign-in method)
- Email verification required (Console → Auth → Settings)
- Security rules lock down user data (Console → Firestore → Rules)
- Storage rules secure file access (Console → Storage → Rules)
- API key restricted (Console → Cloud Console → Credentials)
- No secrets in frontend (Console → Service Accounts; third-party dashboards)
- Monitoring + budget alerts enabled (Console → Performance & Billing)
Final Word
You don’t need to be a developer to make a Firebase Studio project production-ready.
Check key areas in the console.
Paste the right prompts into Studio.
That’s enough to lock down your rules, control your costs, and clean up your app for launch.
And that’s how you turn a vibe-coded prototype into a secure, production-ready app without writing a line of code. 🚀